Several years ago, we wrote up a blog post titled "5 Ways to Avoid Being Blacklisted" that gives some basic tips on how to keep a mail server running smoothly and limit the potential for it to get blacklisted by various spam services. The information in that post is still very relevant, but there are several other things system administrators can do to lock down their SmarterMail servers and protect the reputation of the IP addresses used for sending and receiving mail. But before we quickly run through the points from that blog post, this really needs to be said:
The most important thing you can do to keep your SmarterMail server secure is to make sure you are running the most recent version. We are constantly making changes and updates, and adding new features, to accommodate the ever-changing internet. When Microsoft changes how Outlook works -- and they do that more often than you think -- we have to adapt to those changes. The same holds true for changes in, and updates to, browser and client security. Speaking of changes and new features, here's a little teaser for those of you who read our blog: our next release will include a new integration of Windows Defender, allowing it to run alongside ClamAV or as a standalone service. SmarterMail will communicate with Windows Defender directly to check all incoming and outgoing emails as well as file uploads for draft messages, uploads to File Storage, and uploads to Online Meetings!
As for the blog post referenced above, it touches on doing the following:
- Lock down users and mailboxes, which includes setting up password policies for users, requiring SMTP authentication, and then throttling and spam checking outgoing messages.
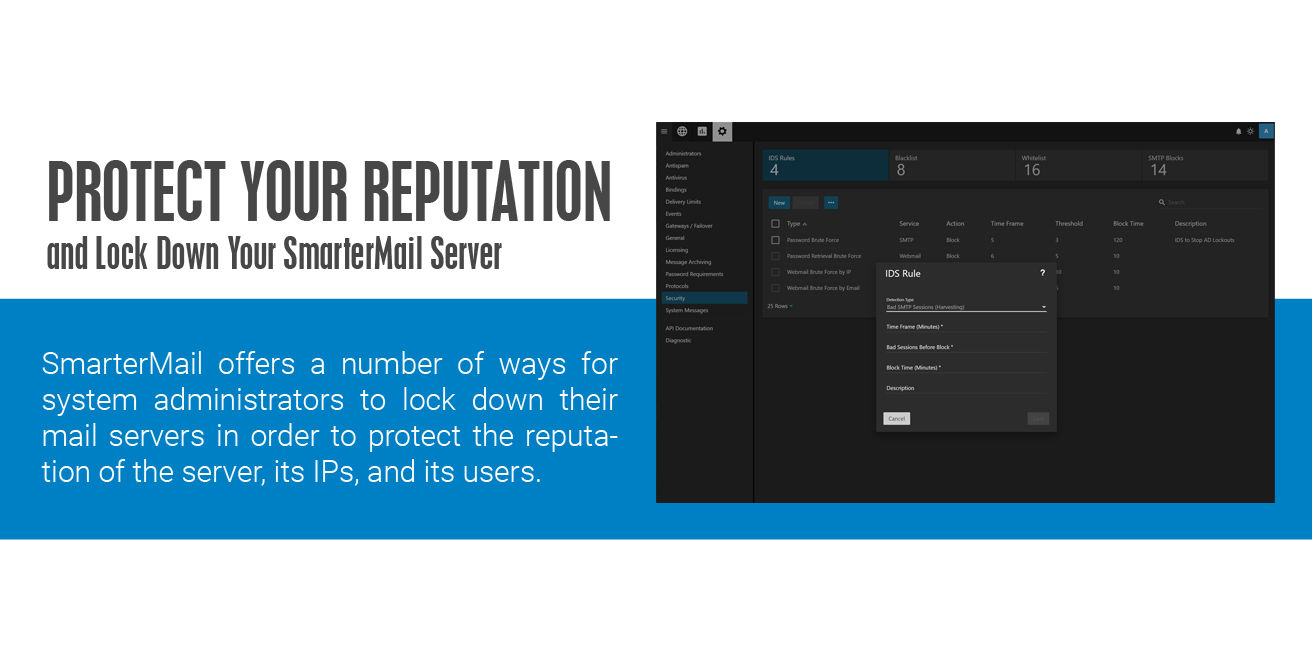
- Set up IDS Rules such as Internal Spammer, which can block or quarantine mass messages that are sent in a short period of time, and Bad SMTP Sessions, which helps eliminate email harvesting attacks on the server.
- Use System Events so that you can be notified when potential issues are occurring such as when system memory spikes or the spool count increases beyond a certain point, which can indicate someone is spamming.
- Lock down mailing lists by limiting who can administrate lists and who can post to lists, or even limit the number of mailing lists a domain can have.
- Watch your reports as they help you keep an eye on server performance, from message traffic to the amount of spam being caught, and much, much more.
Our help documentation offers some additional advice on how to lock down your server, complete with steps on how to make the settings changes referenced. This includes:
- Disabling Catch-All Accounts – Catch-all accounts provide email harvesters with a "valid" address that can be used for future spam attacks, even if the address they are sending to doesn't actually exist. Disabling catch-all accounts, therefore, removes that validation and can help prevent future attacks.
- Restricting Bounces and Auto-responders – Spammers will sometimes spoof known spam trap accounts used by antispam services or RBLs. If you have unrestricted bounces or auto-responders set up, those messages are sent to those spam trap accounts and could possibly trip whatever triggers are in place, thereby getting the IP of your mail server blacklisted. Bounces and auto-responders should be limited to only those accounts that pass SPF checks, if not disabled entirely.
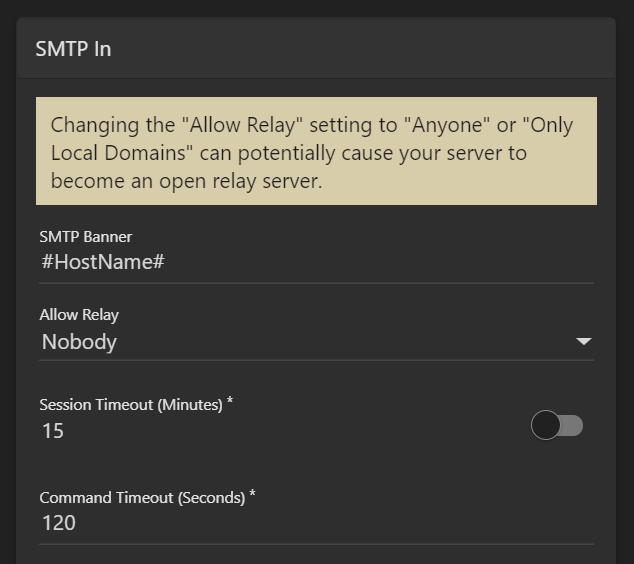
While the above tactics are all a great start, there is more a system administrator can do to protect the integrity of the server and of the IP addresses used on the server. The following settings are all available under Settings > Protocols when you are logged in as a system administrator.
- Disallow Relay – It is STRONGLY recommended that Allow Relay for your SmarterMail server is set to NOBODY. This restricts sent mail to only work via SMTP authentication and that only accounts on the SmarterMail server can send email through the server. (Except for whitelisted Ips.) Having an open relay is a surefire way to find your SmarterMail server blacklisted as abuse of open relays is a tactic as old as email spam itself.
- Require Auth Match – This forces a user's FROM address to match their SMTP authenticated address, either by matching the entire email address or by matching just the domain. (Based on what you set.) This protects the mail server by ensuring SmarterMail users cannot set up spoofed email accounts in an email client, then sending messages using those spoofed accounts.
- Enable domain's SMTP auth setting for local deliveries – This setting will enforce SMTP authentication for all local deliveries. For example, mail from user1@example.com to user2@example.com must be authenticated even though the message is bound for local delivery.
There are just a few of other things that we'd encourage in addition to the above:
- Enable SMTP Authentication - Requiring SMTP authentication for the domains on your server(s) helps mitigate the potential for spoofed messages being sent as senders are required to authenticate their credentials when sending messages through the server. You can even make this part of your Domain Defaults, so any new domain added has it enabled automatically.
- Enable Spool Filtering for SPF - In the Antispam Settings for the server, make sure your SPF check has "Enable Spool Filtering" enabled. SPF is a method of verifying that the sender of an email message went through the appropriate email server when sending their message. As more and more companies add SPF information to their domain DNS records, this check will prevent spoofing at an increasing rate.
- Enable DMARC policy compliance check - We have a pretty thorough blog post on Understanding SPF, DKIM and DMARC that goes over each antispam measure, explaining what they are and how they work, and why they're important. Put simply, DMARC builds upon BOTH SPF and DKIM to ensure that, when an email is received, it's actually sent from who is supposed to have sent it. You can even get reporting, which can be very helpful. One service that offers this, along with a large number of other tools, is MXToolbox. The MXToolbox Delivery Center offers a comprehensive set of reports for your sending domain, allowing you to monitor email delivery information and improve your overall message deliverability.
- Disable old SSL/TLS encryption - TLS 1.0/1.1 is quickly becoming deprecated across the internet. As such, some mail services are beginning to deny connections to and from servers that still have TLS 1.0/1.1 enabled. This, obviously, has serious implications when trying to send and receive email. As such, you'll want to disable support for TLS 1.0/1.1 and ensure you're using the most recent TLS and SSL versions.
- Upgrade Windows Server - Along with the above, you'll want to make sure you're running a current version of Windows Server as some older versions of Windows Server do not support any version of TLS newer than 1.1. We strongly recommend you run Windows Server 2019. However, in order to conform to TLS standards, Windows Server 2016 and above should suffice.
- Keep Windows updated - This may seem like a no-brainer, but it is vitally important. Keeping your system updated with all the latest hot fixes and patches from Microsoft is one of the single most important things you can do as a system administrator.
Finally, there's user education.
Some would argue this is the most important thing you can do to protect your mail server as, no matter what you do on the back end, you still have to contend with the people who use email. As such, while your server may be set up perfectly, there's always user error to contend with. That's where user education comes in. Whether it's weekly training sessions, newsletter items, mentions during team meetings or whatever, making sure people know what NOT to do when accessing their email is one more vital component to your overall security policy. Below are a few things you'll want to make known:
- Be careful with website links - Users should never click links in emails from senders they don't know. Links can take someone to a phishing site, can download malware and more. If someone isn't familiar with who is sending them an email, they should click any links in that email. a nice trick: hover over links in emails to see where they actually go. If they redirect or show a different address than the link text, do NOT click them.
- Be even more careful with file attachments - Just as with links, users should never open any attachments that come from someone they don't know. Often times, file attachments may say they're one ting -- a .PDF for example -- but they're actually executable files. Even things like Word and Excel files can be harmful to a user's system or your network as a whole.
- Be mindful of the message - An email from the IRS saying there's a problem with your taxes is almost assuredly NOT from the IRS. Most emails asking you for personal information or to log in to a service to verify information are simply phishing emails. Most legitimate organizations will not send you any emails asking for personal information without you first asking them to. Any government organization will send you a letter or contact you via the phone.
- Use a strong password - Use of a password vault, like LastPass or 1Password, is a great way to automatically generate and store very strong passwords for all your online activity. These services are even portable so they can follow you to other computers, mobile devices and more.
- User Two-Factor Authentication - Many services will offer secondary ways to verify you when you log in. This will generally entail entering a security code sent via email or text message. Whenever possible, enable Two-Factor Authentication, especially for critical services like banks, online ordering, payment processing (e.g., PayPal), etc.
Of course, there are many, many other things you can instruct people to do. The above, however, is a good start.
As the system administrator, you're the one responsible for maintaining the health and safety of the server. Enacting the above will help drastically reduce the potential for people abusing your mail server, and will go a long way in protecting the reputation of the server, the IP addresses used on the server, and all of your users.